DDoS protection by Cloudflare

WHAT IS DDOS ATTACKS?
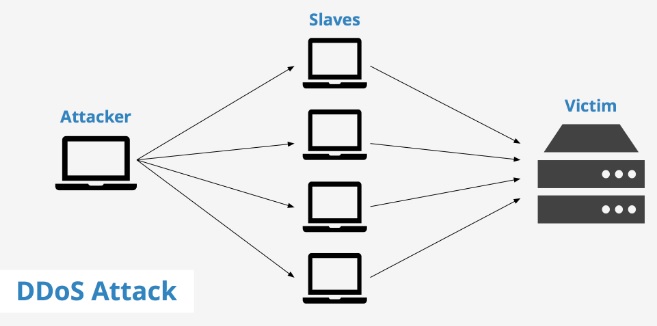
DDOS (Distributed Denial of Service Attack) is hard to prevent and deal with because it is distributed, meaning that you can’t block the requests by IPs unless you shut down the server (which means DDOS does its purpose). Distributed requests are from distributed victim machines in internet so the flood of traffic will eventually slow down your server and make your server denial of services.
HOW DO YOU COPE WITH DDOS ATTACKS?
It is recommended that you keep your Server OS update to date with latest security patch and also security measures are in place e.g. ROOT accounts disabled remotely. Also, the golden rule to avoid DDOS Attacks is to avoid exposing real IPs. It is also a good practice to turn off the PING because the attacker may scan a particular IP range for victims.
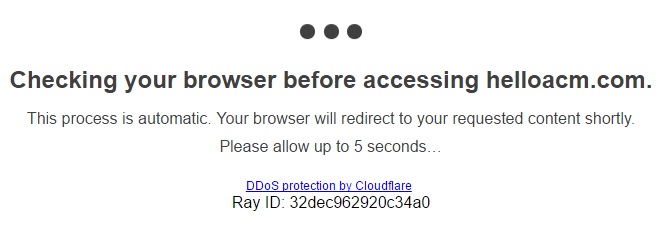
You can use CloudFlare to reverse proxy so the real IPs are hidden. When I noticed the DDOS attacks, I quickly added a page rule to set the security to “I am under Attack”, and that will show a page like this:
Alternatively, you can add a ‘Cache Everything’ page rule, so that the successive contents are served from the CloudFlare edge servers. Both methods immediately bring down the CPU usages, and the servers are back to normal.
Another method is to serve a static cache file as much as you can, so that it doesn’t cost you much CPU resources per request (and you can handle more).
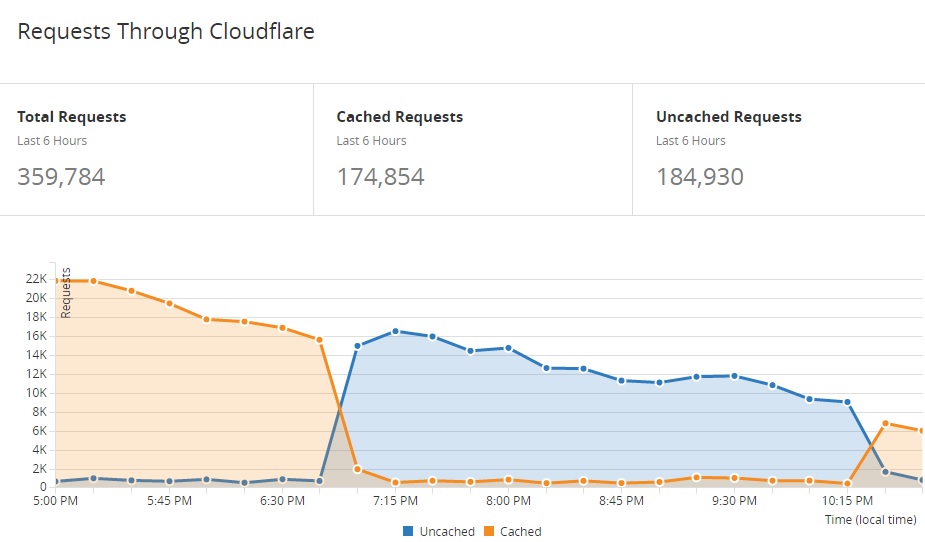
The following CloudFlare traffic statistics show that when DDOS occurs, the uncached requests are increasing, but when I ‘Cache Everything’ the victim API URL, the requests are served from the cloudflare edge servers.